Added a new wiki chapter to the security-misc wiki page just now:Optional Features .
It’s suggesting to check optional features by security-misc (security related, commented-out by default sysctl and kernel parameters).
This includes kernel.unprivileged_userns_clone=0, user.max_user_namespaces=0.
Also added a link to that wiki chapter on the System Hardening Checklist wiki page just now.
The question arises, is it worth it? What’s better:
A) kernel.unprivileged_userns_clone=1 + sandbox enabled; OR
B) kernel.unprivileged_userns_clone=0 + sandbox disabled?
I do not know about appimage. For flatpak, I have been suspicious about their sandbox ever since I read flatkill website (https://flatkill.org/ and https://flatkill.org/2020/ ). Also see Linux | Madaidan's Insecurities .
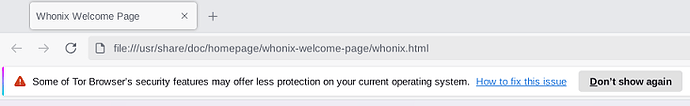
Either way, today I started getting a warning saying that tor browser might not be as secure in my operating system configurations. This was because I set kernel.unprivileged_userns_clone=0 using previous instructions. See Security features warning links to Firefox installation support page with incomplete info (#43101) · Issues · The Tor Project / Applications / Tor Browser · GitLab and Install Firefox on Linux | Firefox Help .
I deleted /etc/sysctl.d/99-disable-unpriv-userns.conf (created using previous instructions), and now I do not get the warning. So I guess that is another reason to prefer kernel.unprivileged_userns_clone=1.
1 Like
Patrick
November 6, 2024, 5:12pm
25
Not enabling unprivileged namespaces will create a Firefox warning message.
Quote Security/Sandbox/Specifics - MozillaWiki
We’re using unprivileged user namespaces for additional security where available;
Also mentioned on Install Firefox on Linux | Firefox Help
If unpriviledged namespaces are disabled, this can also cause a warning for Tor Browser, that was reported here:
Patrick
January 12, 2025, 5:29pm
26
Documented in the wiki just now: